It has been noted that cracked software is infecting users of Apple macOS with a stealer malware that was not previously described. This malware is capable of harvesting information about the machine as well as bitcoin wallet data.
Kaspersky, which discovered the artifacts in the wild, stated that they are intended to target computers that are running macOS Ventura 13.6 or later. This indicates that the malware is capable of infecting Macs that are based on silicon processor designs from both Apple and Intel.
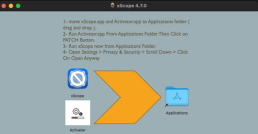
The attack chains make use of disk image (DMG) files that have been booby-trapped. These files contain a program called “Activator” as well as a pirated version of legitimate software like xScope.
It is strongly recommended that users who end up opening the DMG files move both files to the Applications folder, then run the Activator component to apply a patch that is supposed to be applied, and finally start the xScope application while doing so.
Launching Activator, on the other hand, allows it to execute a Mach-O binary with elevated rights in order to launch the modified xScope executable. This is accomplished by displaying a prompt that asks the victim to provide the password for the system administrator.
“The trick was that the malicious actors had taken pre-cracked application versions and added a few bytes to the beginning of the executable, thus disabling it to make the user launch Activator,” according to security researcher Sergey Puzan.
The subsequent step involves establishing communication with a command-and-control (C2) server in order to retrieve a script that has been encrypted. A third-level domain name is created by mixing words from two hard-coded lists and adding a random sequence of five letters. The C2 URL, on the other hand, is produced by merging these two sets of words.
Important Aria Automation Vulnerability Patched by VMware
Aria Automation (formerly vRealize Automation) has a serious security hole that might let an authorized attacker access remote organizations and workflows without their knowledge. VMware has already warned its customers about this hole.
The “missing access control” vulnerability, which is owned by Broadcom, has been identified and awarded the CVE identifier CVE-2023-34063 (CVSS score: 9.9).
It was the Scientific Computing Platforms team at the Commonwealth Scientific and Industrial Research Organization (CSIRO) that found and reported the security hole.
Here are the versions that are affected by the vulnerability:
VMware Cloud Foundation (4.x and 5.x) and VMware Aria Automation (8.11.x, 8.12.x, 8.13.x, and 8.14.x)
“The only supported upgrade path after applying the patch is to version 8.16,” claimed VMware. “If you upgrade to an intermediate version, the vulnerability will be reintroduced, requiring an additional round of patching.”
Critical Code Execution Bug Revealed by Atlassian
There was a major remote code execution (RCE) vulnerability that affected Confluence Data Center and Confluence Server, and this development comes after Atlassian released remedies for more than twenty vulnerabilities.
A CVSS score of 10.0 indicates that the vulnerability, CVE-2023-22527, is very serious. This issue impacts versions ranging from 8.0.x to 8.5.3, as well as versions 8.1.5 to 8.3.x. Keep in mind that the vulnerability does not impact 7.19.x LTS versions.
“A template injection vulnerability on out-of-date versions of Confluence Data Center and Server allows an unauthenticated attacker to achieve RCE on an affected version,” the business from Australia stated.
Versions 8.5.4, 8.5.5, 8.6.0, 8.7.1, and 8.7.2 (Data Center only) of Confluence have fixes for this issue. It is advised that users who are on outdated instances update their installations to the most recent version that is available.
MANAGED CYBERSECURITY SOLUTIONS
Rhyno delivers a range of activities that combine to fully protect your infrastructure and data from cybercriminals, anywhere and everywhere, 24/7/365.
About Rhyno Cybersecurity Services
Rhyno Cybersecurity is a Canadian-based company focusing on 24/7 Managed Detection and Response, Penetration Testing, Enterprise Cloud, and Cybersecurity Solutions for small and midsize businesses.
Our products and services are robust, innovative, and cost-effective. Underpinned by our 24x7x365 Security Operations Centre (SOC), our experts ensure you have access to cybersecurity expertise when you need it the most.