Industrial Control Systems (ICS) encompass the technologies employed to monitor and manage industrial processes. Supervisory Control and Data Acquisition (SCADA) systems are among these systems, which form a subset of ICS.
When contrasting these systems with conventional IT systems, their unique characteristics become evident. Consequently, applying standard security controls designed for older systems can be a formidable task. Fortunately, there are resources available to assist in safeguarding these systems. This ensures that ICS owners do not have to rely on assumptions or undertake blind security measures.
The Center for Internet Security and the National Institute of Standards and Technology (NIST) both publish manuals and controls specifically for ICSes.
[FREE E-BOOK] The Definite Blueprint for Cybersecurity in Manufacturing
A step-by-step guide for securing your company against cyber attacks.
National Institute of Standards and Technology
The NIST 800-53 serves as the cornerstone of the Risk Management Framework (RMF) for federal systems. Within this framework, specific controls cater to the unique requirements of business technology systems. In its latest iteration, the NIST Special Publication 800-82, Guide to Industrial Control Systems (ICS) Security, has reached Revision 2.
Given the distinctive challenges posed by ICSes, often stemming from their reliance on older legacy systems, the creation of 800-82 specifically addressed these system types. The publication outlines several security objectives for ICS adoption, which can be found within the contents of 800-82.
- Limiting logical access to and use of the ICS network
- ICS network and device physical access restrictions
- Preventing abuse of specific ICS components
- Preventing illegal data modification
- Identifying security incidents and occurrences
- Preserving functioning under challenging circumstances
- Restoring the system following a mishap
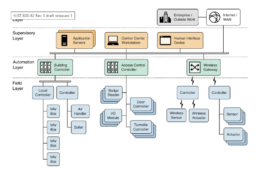
The security control families listed in 800-82 will be familiar to those who are familiar with the RMF:
- Access Control Education and Awareness
- Accountability and auditing
- Security Evaluation and Approval
- Identification and Authentication Configuration Management Contingency Planning
- Response to Emergencies Maintenance
- Protecting the media
- Planning for physical and environmental protection
- Employee Security Risk Analysis
- Acquiring systems and services
- Program Management for System and Communications Protection, System and Information Integrity
- Privacy controls
The applicable controls for each category are listed for individual households, encompassing both administrative and technical restrictions. Proper classification and evaluation of the ICS will determine the suitable controls for a specific environment. Once this determination has been made, the controls should be implemented, thoroughly checked and tested, and consistently monitored for effectiveness.

Internet Security Center
In order to enhance the security of IDS systems, the Center for Internet Security (CIS) has developed CIS Controls Version 7. These controls were crafted based on seven fundamental principles:
- Address emerging threats, new technologies, and evolving IT mission/business requirements effectively.
- Enhance the focus on crucial aspects such as application whitelisting, encryption, and authentication.
- Align more closely with existing frameworks.
- Ensure each sub-control employs a single “ask” to improve consistency and clarity.
- Establish a foundation for a rapidly expanding ecosystem of associated products and services derived from CIS and the market.
- Implement minor structural adjustments, improving the format and layout.
- Incorporate insights from a global community of supporters, adopters, and volunteers, reflecting their valuable perspectives.
The controls are further organized into three primary regions, consisting of a total of 20 subsections. In conjunction with the controls, CIS has provided the V7 implementation guide, which serves as a companion document. This ICS-specific guide enables the customization of controls to suit the specific SCADA environment. In the following sections, we will delve into each of the 20 control sets in greater detail.
Basic controls
1. Asset Inventory and Hardware Control
Considered as one of the most critical controls, this entails maintaining an exhaustive inventory of all system components. Without comprehensive knowledge of every element within your system, evaluating and protecting it effectively becomes challenging.
2. Software Inventory and Asset Management
Similar to hardware, the software components of your system also require diligent inventory and asset management. The software possesses unique vulnerabilities; without a comprehensive understanding of these weaknesses within your architecture, tracking and addressing them becomes problematic.
3. Continuous Vulnerability Management
SCADA environments often comprise numerous embedded systems that control critical infrastructure components. Updating and patching these systems can pose challenges, as industrial systems typically have limited service windows due to uptime requirements. When formulating a vulnerability management strategy tailored for the ICS environment, it is essential to consider these constraints and requirements.
4. Controlled Use of Administrative Privileges
Access restrictions are vital in preventing unauthorized users from gaining excessive privileges. To ensure security, administrative accounts must adhere to the separation of duties principles and enforce strong password restrictions. Implementing these measures helps maintain control and safeguard the system from unauthorized access.
5. Secure Configuration of Mobile Devices, Laptops, Workstations, and Servers
CIS provides benchmarks to enhance the security of IT systems. However, it’s important to note that these benchmarks may not always consider the non-standard operating systems used in ICS environments. To ensure the implementation of system-specific best practices, it is crucial to adhere to industry standards and consult the relevant manuals or vendor websites for comprehensive guidance.
6. Maintenance, Monitoring, and Analysis of Audit Logs
Embedded systems may not inherently possess the same auditing capability as conventional IT systems. Additionally, forwarding these logs to a centralized monitoring system can pose challenges. To overcome these limitations, leveraging a Security Information and Event Management (SIEM) system specifically designed for ICS environments can offer significant advantages. Such a specialized SIEM can enhance the maintenance, monitoring, and analysis of audit logs in the ICS context.
7. Fundamental Safeguards
Protections for Email and Web Browsers
Email clients and web browsers are particularly vulnerable to security risks. Based on the most recent security risks, the CIS provides benchmarks that are used to harden them.
8. Malware Protection
As mentioned earlier, maintenance of ICSes can be challenging due to uptime requirements. However, it is crucial to prioritize malware protection. Ensure that antivirus and malware signatures are regularly updated when implementing malware protection. This ensures the system remains equipped with the latest defences against emerging threats.
9. Network Ports, Protocols, and Services Have Restrictions.
Identify all of the ports, protocols, and services the ICS will require to function as intended when you list the assets. Use only the open ports that are necessary for the system to run correctly.
10. Capabilities for Data Recovery
Data backup is essential in ICS contexts and in conventional enterprise environments. In some SCADA setups, automated backups may prove challenging; keep this in mind when describing backup and recovery protocols.
11. Configuring Network Devices Securely, Including Firewalls, Routers, and Switches
In SCADA environments, secure network devices are equally as vital, if not more so. Firewall traffic must only pass through authorized ports. The default setting ought to be “Deny”. Remove the default login information and accounts from network devices. Put multi-factor authentication into practice.
12. Boundary Protection
Only trusted channels should be used for the transfer of information. Strategically position control devices to effectively manage the flow of information. This includes securing DMZ perimeters and implementing proxies, IDS/IPS, firewalls, and gateways to ensure robust boundary protection.
13. Data Protection
ICSes do not store conventionally sensitive data like HIPAA, PII, or financial information, but they do collect sensitive data like valve readings, flow, temperature, pressure measurements, and even commands for logic control devices that are deemed sensitive and need to be protected. Implementing sniffers, anomaly detection tools, and encryption for data at rest is a powerful defence.
14. Controlled Access Based on the Need to Know
Even ICSes can be segmented to segregate data into regulated segments for controlled access based on the need to know. By using ACLs, you can ensure that only authorized workers may access the data they need to.
15. Control of Wireless Access
To maintain control, ensure that wireless traffic is routed through managed networks, preferably private ones. To safeguard network traffic, employing at least AES or ECC encryption for wireless communication is imperative.
16. Account Control and Monitoring
- Only use shared passwords and accounts when necessary.
- Establish a procedure for changing shared account passwords and deleting accounts immediately after any employee leaves the workforce.
- Discontinue any programs that use cleartext or simple security authentication. When this isn’t practicable, employ unique credential sets and keep track of how they’re being used.
- Demand strong passwords
- L.ock accounts automatically after inactivity intervals
Organizational controls
17. Implementation of a Security Awareness and Training Program
Users often represent the weakest link in the security chain. However, establishing an effective training program can mitigate the risks they pose to the internal network. By providing comprehensive security awareness and training, users can gain the necessary knowledge and skills to make informed decisions and actively contribute to reducing potential security threats within the organization.
18. Security for Application Software
Applications can have vulnerabilities that need to be identified and addressed. It is recommended to perform debugging and static code analysis to locate these flaws effectively.
19. Incident Response and Management
Even with robust security procedures in place, there is still a possibility of falling victim to security threats. Therefore, it is crucial to have an incident response team prepared and equipped to respond to any incidents that may occur swiftly.
20. Red Team Exercises and Penetration Tests
A valuable technique to validate the effectiveness of security protections is to conduct red team exercises and penetration tests after their implementation.
Conclusion
Because of their unique characteristics, ICSes can make implementing security more challenging than in conventional IT environments. These benchmarks and procedures from NIST and CIS both aid in developing a strong security posture.
MANAGED CYBERSECURITY SOLUTIONS
Rhyno delivers a range of activities that combine to fully protect your infrastructure and data from cybercriminals, anywhere and everywhere, 24/7/365.
About Rhyno Cybersecurity Services
Rhyno Cybersecurity is a Canadian-based company focusing on 24/7 Managed Detection and Response, Penetration Testing, Enterprise Cloud, and Cybersecurity Solutions for small and midsize businesses.
Our products and services are robust, innovative, and cost-effective. Underpinned by our 24x7x365 Security Operations Centre (SOC), our experts ensure you have access to cybersecurity expertise when you need it the most.