The NIST Cybersecurity Framework illuminates a realm where digital threats are abundant in the field of cybersecurity. Before delving into NIST standards, it’s crucial to have a firm grasp on the many moving parts that comprise an effective cybersecurity posture.
Understanding the Basics
What is NIST?
The National Institute of Standards and Technology (NIST) stands as a renowned authority in shaping cybersecurity standards. More than mere guidelines, NIST standards form a comprehensive framework meticulously crafted to fortify organizations against the ever-evolving landscape of cyber threats.
The Pillars of NIST Cybersecurity Standards
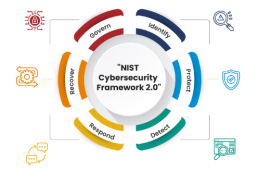
- Identify
-
-
- The first step is recognizing the lay of the land.
- In this phase, organizations define and catalogue their assets, assess vulnerabilities, and comprehend potential risks.
-
- Protect
-
-
- Think of it as putting a shield around your fortress.
- Protecting assets involves implementing safeguards to ensure the integrity, confidentiality, and availability of critical information.
-
- Detect
-
-
- Spotting threats before they strike is the name of the game.
- Detection mechanisms are crucial for identifying anomalous activities and potential security incidents in real time.
-
- Respond
-
-
- When the alarm sounds, it’s time to take action.
- A swift response plan is essential for mitigating the impact of a cybersecurity incident and getting back on track.
-
- Recover
-
- Bouncing back stronger after a setback.
- The recovery phase involves restoring systems to normal operation and learning from the incident to enhance future resilience.
The Flexibility Factor
A remarkable aspect of NIST Cybersecurity Standards is their adaptability. Far from being a rigid set of rules, they present a flexible framework that organizations can tailor to meet their unique needs.
A Deep Dive into NIST Cybersecurity Standards
As we conclude this exploration into the basics of NIST Cybersecurity Standards, it’s evident that this framework offers a holistic approach to safeguarding against cyber threats. In the upcoming section, we’ll delve deeper into each pillar, uncovering practical insights and strategies to implement NIST standards effectively.
Evaluating IT Cloud Services Before You Choose
In conclusion, the evaluation of IT cloud services is a meticulous process that demands attention to detail. As businesses increasingly embrace the cloud, making an informed choice ensures a seamless transition and sets the foundation for long-term success. In the next part, we’ll delve into the specific benefits and potential pitfalls of various cloud services, guiding you toward a well-rounded decision.
Understanding the Benefits
- Cost-Efficiency
-
-
- The adage “get more bang for your buck” perfectly captures the cost efficiency of cloud services.
- Cloud computing eliminates the need for hefty upfront investments in physical infrastructure, enabling businesses to allocate resources more effectively.
-
- Global Accessibility
-
-
- In the digital age, having your data at your fingertips is not a luxury but a necessity.
- Cloud services provide global accessibility, enabling teams to collaborate seamlessly, regardless of their geographical locations.
-
- Automatic Updates
-
-
- Imagine having your software always up to date without lifting a finger.
- Cloud services offer automatic updates, ensuring that businesses are equipped with the latest features and security patches.
-
- Enhanced Collaboration
-
- Collaboration is the name of the game in the modern workplace.
- Cloud platforms facilitate real-time collaboration, allowing team members to work concurrently on documents and projects.
Navigating the Potential Pitfalls
- Security Concerns
-
-
- Addressing security concerns is akin to walking a tightrope in the cloud.
- While cloud providers heavily invest in security, businesses must actively manage access controls and encryption protocols to mitigate risks.
-
- Downtime Issues
-
-
- Downtime is the nemesis of productivity.
- Despite high reliability, cloud services are not immune to downtime. Businesses need contingency plans to minimize the impact of potential disruptions.
-
- Data Transfer Bottlenecks
-
-
- The speed of data transfer can make or break the cloud experience.
- Bandwidth limitations or geographical constraints can result in slow data transfer, impacting performance.
-
- Vendor Lock-In
-
- Choosing a cloud provider is like choosing a dance partner; you want to be sure it’s a good fit.
- Businesses must exercise caution regarding potential vendor lock-in, ensuring they can easily migrate their data if needed.
Evaluating IT Cloud Services: Final Reflections
In concluding our exploration, evaluating IT cloud services demands a balanced consideration of both benefits and challenges. While the cloud offers doors to unprecedented efficiency and innovation, businesses must tread carefully to navigate potential pitfalls. As you embark on your cloud journey, remember that understanding your unique business needs acts as the compass guiding you through the cloud maze.
Ready to soar into the cloud? Make an informed choice and unlock the full potential of IT cloud services.
MANAGED CYBERSECURITY SOLUTIONS
Rhyno delivers a range of activities that combine to fully protect your infrastructure and data from cybercriminals, anywhere and everywhere, 24/7/365.
About Rhyno Cybersecurity Services
Rhyno Cybersecurity is a Canadian-based company focusing on 24/7 Managed Detection and Response, Penetration Testing, Enterprise Cloud, and Cybersecurity Solutions for small and midsize businesses.
Our products and services are robust, innovative, and cost-effective. Underpinned by our 24x7x365 Security Operations Centre (SOC), our experts ensure you have access to cybersecurity expertise when you need it the most.