IBM conducts an annual Data Breach Report providing businesses with concrete figures regarding the financial impact of data breaches. This valuable information empowers companies to make informed decisions about enhancing their security measures based on factual insights.
The research for this study was undertaken by the Ponemon Institute and sponsored, analyzed, and released by IBM Security. The 18th edition of the study, published in 2023, delved into 553 breaches across 16 countries and 17 industries.
Etay Maor, Senior Director of Security Strategy at Cato Networks, emphasizes, “We talk a lot about security problems and how to fix them.” This study outlines threats and their solutions with numerical data, providing ample evidence to support claims about the financial impact of a threat actor, a solution, or a specific process.
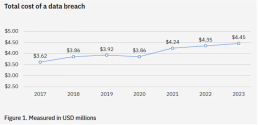
Key Finding #1: The average cost of a data breach reached a new peak in 2023, yet companies aren’t matching this increase with equivalent investments in security.
Since 2017, the average cost of a data theft has exhibited a nearly continuous upward trend. In 2017, the average cost was “only” $3.62 million, and it has surged to a peak of $4.45 million in 2023. This represents a 15% increase in the average cost of a breach over the past three years.
It appears that the costliest breaches occur in the healthcare sector ($10.93 million), followed by finance ($5.9 million), drugs ($4.82 million), energy ($4.78 million), and manufacturing ($4.73 million).
The average cost of an attack on healthcare is nearly twice as high as the next industry. This is likely due to the multitude of attack vectors against healthcare organizations, their prioritization of operational outcomes over security, the high value of PHI data to threat actors, and the stringent regulations governing healthcare, which may result in more expensive consequences for non-compliance.
Maor says, “Attacking healthcare organizations can also be a way to get something done.” Perpetrators may steal an individual’s medical records to commit identity theft, launch attacks on banks or insurance companies, or engage in other malicious activities.
The breaches incurring the highest costs took place in the US ($9.48 million), the Middle East ($8.07 million), and Canada ($5.13 million). Typically, threat actors target affluent regions, explaining why most of the countries they focus on boast high GDPs.
IBM Security also conducted a comparison between the average cost and the number of breaches, categorized by the initial attack route. Here are some noteworthy insights:
- Individuals posing a threat to organizations most frequently exploit phishing as their entry point, which is also the second most expensive method for organizations ($4.76 million).
- The use of stolen or compromised passwords is another prevalent practice, incurring a significant cost of $4.62 million.
- Malicious insiders are a fairly less common attack vector. However, they are the costliest breach ($4.9M).
Maor adds, “A zero-trust approach makes it easy to stop many of these attack vectors.” Granting users only the necessary permissions, such as accessing customer data or administrative privileges, can be an effective strategy.
However, only 51% of companies indicated, when surveyed, that they would increase their spending on security following a breach. To bridge this gap, security professionals should leverage data, such as the insights from the IBM Security report, to communicate and quantify the value of security to top executives and the board effectively.
Among those willing to increase security spending, 50% would allocate funds to planning and testing incident response, 46% to employee training, and 38% to tools designed to detect and mitigate threats.
Key Finding #2: Implementing a DevSecOps approach, establishing incident response teams, and incorporating automation and AI resulted in significant cost savings.
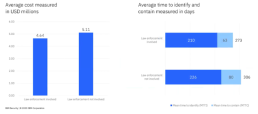
According to a study by IBM Security, the average cost of a data breach increases when AI and robotics are employed for security. Organizations that heavily invested in and utilized AI and automation in their systems saved an average of $1.76 million per breach compared to those that didn’t use AI and automation at all. Additionally, they reduced the time it takes to respond to a breach by 108 days.
Companies that employed high levels of DevSecOps or incident response planning and testing saved a significant amount of money compared to those with low levels or none at all:
Companies using a DevSecOps method saved $1.68 million.
With an incident response team and regular testing, the company saved $1.49 million.
Key Finding #3: It cost more and took longer to stop breaches when data was stored in more than one place.
39% of the stolen data was distributed across various locations, including public, private, mixed, and on-premises. The breach costs for this data were also $750,000 higher than others.
Additionally, it took 291 days to halt the breach, marking the lengthiest duration for this data. This exceeded the normal timeframe by 15 days.
It’s crucial to note that this doesn’t imply the cloud is less secure. However, due to its novelty and complexity, it requires a deeper understanding. Therefore, employing DevSecOps and integrating security into the initial stages of architecture development is essential.
Finding #4: Organizations that discovered the breach themselves were able to mitigate it more swiftly than those relying on a third party or an attacker (241 days vs. 273 days for a third party and 320 days for an attacker). This efficiency stemmed from the collaboration between internal security teams and law enforcement in identifying and addressing the breach.
Moreover, the associated average costs were lower: $4.3 million when the company found the breach, $4.68 million when a reputable third party did so, and $5.23 million when an attacker identified it. The time it takes and the financial impact on the company are closely intertwined.
Both the standard cost and the time required to discover and contain the breach were significantly reduced when law enforcement was involved. Their assistance resulted in a cost of $4.64 million compared to $5.11 million when they were not involved. Additionally, the breach was resolved in 276 days instead of 306 days.
Another compelling reason for businesses to involve law enforcement when attacked is that law enforcement agencies globally, including the FBI, have the capacity to take action against these threat actors. In contrast, businesses and individuals lack such authority.
In conclusion, taking into account the insights from this report, here are the key recommendations for all groups:
-
Security Integration in Development:
- Include security in all stages of hardware and software development, testing frequently.
- Utilize a DevSecOps method.
- Apply “secure by design” and “secure by default” principles during the initial design.
- Enforce consistent rules in cloud settings.
- Conduct pen testing or application testing.
- Ensure data security in mixed cloud environments.
-
Data Management in Hybrid Cloud Settings:
- Take control of information in hybrid cloud settings.
- Safeguard data as it moves between services, systems, and applications.
- Use methods for monitoring data activity.
- Incorporate AI and robotics in security for enhanced speed and accuracy.
-
AI and Robotics in Security:
- Integrate AI and automation into security tools for improved threat detection, response, and investigation.
- Use fully developed AI tools.
- Utilize threat intelligence reports to identify patterns and stay informed about existing threats by integrating key security technologies for smooth workflows and shared insights.
-
Resilience and Incident Response:
- Understand your attack surface and practice incident action to enhance system resilience.
- Assess the vulnerability of your business and market to related attacks.
- Utilize ASM tools or adversary modeling methods to gain an attacker’s view of the risk profile and vulnerabilities.
- Assemble a skilled team proficient in using IR tools and standards.
- Develop and regularly test IR plans.
- Consider hiring an IR vendor on a fee basis to enhance breach response capabilities.
MANAGED CYBERSECURITY SOLUTIONS
Rhyno delivers a range of activities that combine to fully protect your infrastructure and data from cybercriminals, anywhere and everywhere, 24/7/365.
About Rhyno Cybersecurity Services
Rhyno Cybersecurity is a Canadian-based company focusing on 24/7 Managed Detection and Response, Penetration Testing, Enterprise Cloud, and Cybersecurity Solutions for small and midsize businesses.
Our products and services are robust, innovative, and cost-effective. Underpinned by our 24x7x365 Security Operations Centre (SOC), our experts ensure you have access to cybersecurity expertise when you need it the most.