Our cybersecurity posture faces new challenges and opportunities each New Year. The speed at which hostile actors launch advanced persistent attacks makes cyber resilience an ongoing battle. Cybersecurity’s excitement comes from adapting and learning to stay ahead of threats.
Working in a 24/7 industry makes hypervigilance second nature. We always prepare for the next move, adjust strategies, and fight dangers. However, keeping an eye on the most pressing security vulnerabilities is just as important. Why? Knowing these weaknesses isn’t just about defense; it’s about ensuring business continuity in a risk-filled environment.
The Importance of Regular Security Assessments
By detecting vulnerabilities, cybersecurity experts may establish a cyber resilient security posture, however only 35% or 11% have excellent visibility. Over half of firms (51%) have moderate vulnerability visibility.[1]
Regular assessments are one of the best ways to analyze your organization’s security and identify issues. These evaluations thoroughly analyze your organization’s cybersecurity processes and infrastructure and might vary in extent and frequency depending on your needs and risk program maturity.
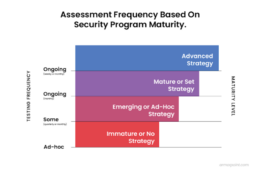
Test Frequency and Security Maturity
- Inadequate Risk Strategy: Assessments are done sporadically.
- Emerging or Ad-Hoc Risk Strategy: Quarterly or monthly assessments.
- Monthly assessments are done to mature or set strategy.
- Advanced Strategy: The risk program includes monthly or weekly assessments, depending on the test.
Common Framework Recommended Testing Frequency
NIST CSF: NIST recommendations change from quarterly to monthly scans depending on the governing framework.
- Payment Card Industry Data Security Standard (PCI DSS) requires quarterly scans.
- HIPAA: HIPAA stresses a well-defined evaluation strategy but does not require specific scanning intervals.
- Types of Regular Assessments#Vulnerability Scans
- Penetration Tests
- Simulations of Breach and Ransomware
- Scan security reputation
- Business Impact Studies
- Assessing security posture
- Routine assessments allow your organization to anticipate security threats and vulnerabilities, like cybersecurity health checks.
Top 6 Vulnerabilities
Now, let’s discuss the vulnerabilities uncovered during frequent security posture assessments and their possible influence on your organization’s security.
Vulnerability Management Program Gaps
A comprehensive vulnerability management approach underpins proactive cybersecurity for your company. It alerts your company to security issues. Without a program, organizations face greater exposure to known vulnerabilities, ineffective patch administration, and inability to prioritize severe vulnerabilities.
Inadequate detection and monitoring
Threats can go undiscovered for long periods if your organization’s detection procedures are inadequate. Without modern Intrusion Detection Systems (IDS) or Security Information and Event Management (SIEM) solutions, threat detection may be delayed or missed, attacker dwell time increased, and data exfiltration increased. Advanced monitoring techniques and tactics are needed to improve this. Modern threat detection and response technology, behavior analytics for anomaly identification, and threat-hunting activities can improve detection capabilities.
Lack of such safeguards slows threat identification and hinders quick response. Maintaining a strong defense against emerging cyber threats requires a sophisticated detection and monitoring system. To remain ahead of cybercriminals’ latest attack vectors and approaches, detection methods must be updated and refined.
Formalized cybersecurity rules and processes are essential for organizations to properly manage security risks. Without these, departments have inconsistent security procedures, weaker incident response capabilities, trouble complying with rules, and more legal, regulatory, financial, and reputational risk. Creating and implementing comprehensive security policies requires clear development and documentation, efficient communication to all personnel, and compliance education.
These rules must be reviewed, updated, and adapted to the changing cyber threat scenario. This also keeps the company’s cybersecurity current. Having well-defined protocols also standardizes security incident responses, limiting impact and expediting recovery after a breach.
Insufficient Testing Practices:Regular testing of security systems and incident response plans is essential for detecting vulnerabilities and preparing for real-world attacks. This involves third-party security evaluations, penetration testing to find vulnerabilities, and incident response planning. Testing is crucial because it finds flaws before attackers do and evaluates security controls.
Regular testing also speeds up incident response and reduces damage. Maintaining a resilient cybersecurity posture that can defend against the latest security threats requires this practice. External reviews by third-party experts typically reveal blind spots that internal teams ignore.
Training and Cyber Awareness: Untrained people can create weaknesses and increase attack risk for a business. Insufficient training causes misconfigurations, human errors, and failure to notice and respond to attacks, weakening security safeguards. To overcome this, security awareness training is essential. Continuous cybersecurity training, professional growth and certifications, and security awareness are vital.
These programs train staff at all levels to recognize and address security concerns. Organizations can reduce human error breaches by informing and monitoring employees. A comprehensive cybersecurity plan requires proactive worker training.
Adopt and Implement Framework
Organizations seeking a systematic security approach must choose and follow a cybersecurity framework. Frameworks provide a security roadmap, ensure industry best practices, and aid regulatory compliance. Your organization’s needs and risk tolerance should be assessed, a suitable framework (e.g., NIST Cybersecurity Framework) chosen, and customized to meet its needs.
Cybersecurity risk management is systematic and rigorous with framework adoption and implementation. They also provide guidance for implementing strong security practices, improving an organization’s security. The framework is customized to meet the organization’s security demands, industry standards, and regulatory constraints.
Understanding and integrating your organization’s risk appetite into your cybersecurity strategy is crucial for effective risk management. Your organization’s risk tolerance affects decision-making and resource allocation. Understanding risk appetite helps align cybersecurity efforts with the organization’s risk tolerance and prioritize security solutions based on risk assessments.
Continuous vigilance is needed to evaluate evolving hazards and adjust security strategies. This method makes cybersecurity proactive, anticipating and reducing risks. By identifying and managing risk, companies may establish a resilient and robust cybersecurity posture that meets their needs and risk tolerance.
After identifying common vulnerabilities, it’s important to prioritize their solutions based on severity and impact. Increase visibility into your organization’s vulnerabilities first. You can prioritize and remediate these risks if detected. An industry-accepted framework like NIST CSF, CIS, or SANS can reduce these risks. These frameworks help firms establish strong cybersecurity practices by analyzing current security measures against the framework’s requirements, creating and implementing suitable policies, and training workers regularly. Continuous monitoring and improvement help identify and fix security problems.
Cybersecurity is a continual commitment to preserving your company’s assets and reputation. Addressing these frequent vulnerabilities found in security posture assessments and remaining watchful can improve your security and lower your risk of assaults.
MANAGED CYBERSECURITY SOLUTIONS
Rhyno delivers a range of activities that combine to fully protect your infrastructure and data from cybercriminals, anywhere and everywhere, 24/7/365.
About Rhyno Cybersecurity Services
Rhyno Cybersecurity is a Canadian-based company focusing on 24/7 Managed Detection and Response, Penetration Testing, Enterprise Cloud, and Cybersecurity Solutions for small and midsize businesses.
Our products and services are robust, innovative, and cost-effective. Underpinned by our 24x7x365 Security Operations Centre (SOC), our experts ensure you have access to cybersecurity expertise when you need it the most.